To control and secure applications, web-services and IoT-devices there must be somekind of mechanism to control identity and levels of authorization, we need identity management. FIWARE implemented some services and tools to allow you to manage authentication and authorization in applications and backend services.
Identity management concepts
The main identity management concepts are:
- Users
- Have a registered account.
- Can manage organizations and register applications.
- Organizations
- Are group of users that share resources of an application (roles and permissions).
- Users can be members or owners (manage the organization).
- Applications
- has the client role in the OAuth 2.0 architecture and will request protected user data.
- Are able to authenticate users using their Oauth credentials (ID and secret) which unequivocally identify the application
- Define roles and permissions to manage authorization of users and organizations
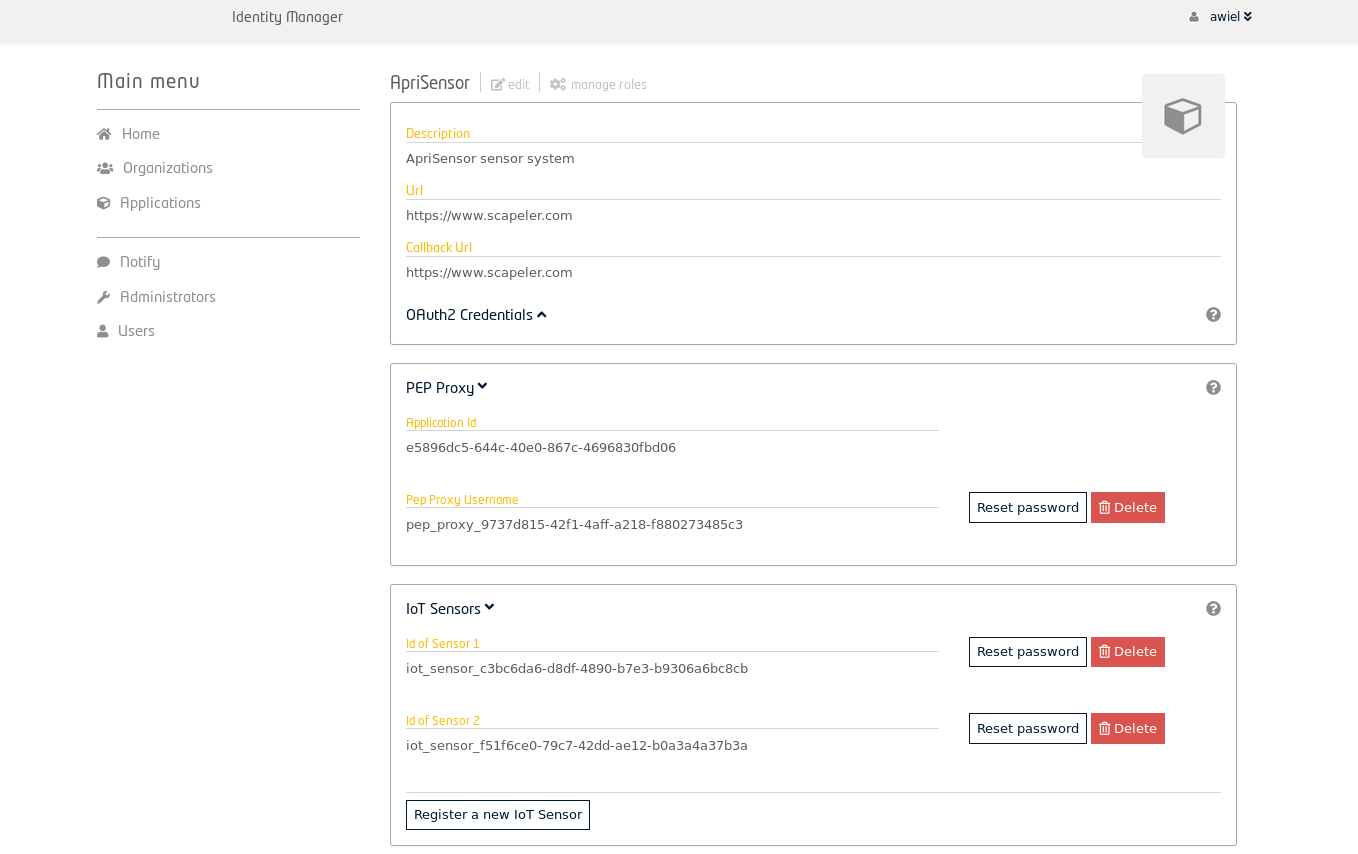
- Can register Pep Proxy to protect backends.
- Can register IoT Agents.
Keyrock – users and permissions
Keyrock is an so called Generic Enabler in Fiware which allow the creation of users and organizations.You can also register new applications in order to use the OAuth2 protocol and manage roles and permissions.
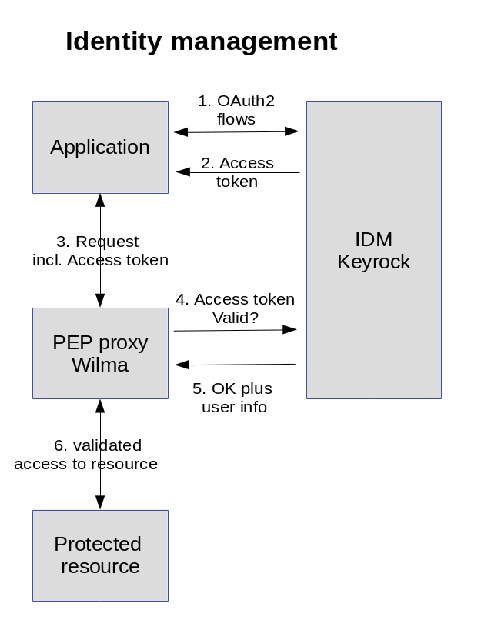
Wilma – PEP proxy
To allow only permitted users or applications to access a REST service a PEP-proxy is placed between the application and the endpoint of the REST-service. The PEP-proxy receives the requests only allowing those with and valid token.
Authentication process
- Identify
- Get an access token
- Request REST-service via PEP-proxy
- PEP-proxy asks if token is allowed for this service
- OK-response from IDM
- Access validated resource
Examples IDM